
Understanding Identity Access Management (IDAM): Safeguarding Digital Frontiers
In today’s increasingly digital world, the safeguarding of sensitive data has become paramount. With the proliferation of online platforms, cloud services, and interconnected devices, the need for robust Identity Access Management (IDAM) systems has never been greater. In this article, we will delve into the intricate world of IDAM, exploring its significance, core components, and the pivotal role it plays in securing our digital identities.
1. Introduction
In a world where data breaches and cyberattacks are prevalent, Identity Access Management, commonly referred to as IDAM, serves as a fortress that guards our digital lives. It is the key to controlling who gets access to what within an organization’s digital infrastructure, ensuring that only authorized individuals have access to sensitive information.
2. What is Identity Access Management (IDAM)?
Identity Access Management, or IDAM, is a framework of policies, technologies, and processes that facilitates the management of digital identities. It encompasses everything from user authentication to access control, providing organizations with the tools they need to protect their valuable assets.
3. The Evolution of IDAM
IDAM has come a long way since its inception. Initially, it focused primarily on basic user authentication. However, with the increasing complexity of digital ecosystems, it has evolved to encompass a wide range of functions, including authorization, role-based access control, and more.
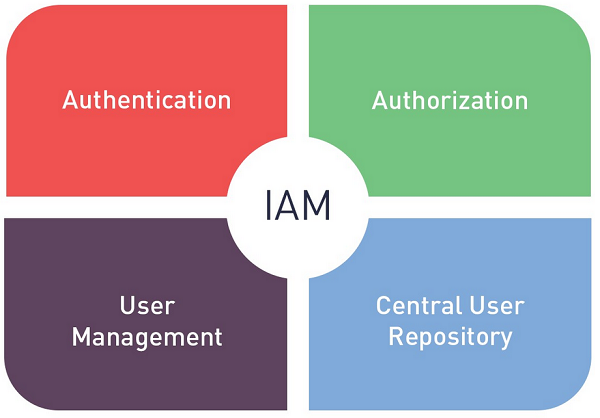
4. Key Components of IDAM
4.1 Authentication
Authentication is the first line of defense in IDAM. It verifies the identity of a user, ensuring that they are who they claim to be. This can involve something as simple as a username and password or more advanced methods like biometrics.
4.2 Authorization
Once a user is authenticated, authorization comes into play. It determines what resources or data the user can access. This is typically based on their role within the organization.
4.3 Single Sign-On (SSO)
SSO simplifies the user experience by allowing users to access multiple systems and applications with a single set of credentials. It enhances security and productivity.
4.4 Identity Governance and Administration (IGA)
IGA involves managing user roles and permissions, ensuring that they align with organizational policies and compliance requirements.
5. How IDAM Works
IDAM systems work by maintaining a directory of digital identities and their corresponding access rights. When a user attempts to access a resource, the system checks their identity and permissions before granting or denying access.
6. Benefits of Implementing IDAM
Implementing IDAM brings several advantages, including improved security, streamlined user management, and enhanced compliance with regulations such as GDPR and HIPAA.
7. IDAM Best Practices
To get the most out of IDAM, organizations should follow best practices such as regular access reviews, strong password policies, and ongoing user training.
8. Challenges in IDAM Implementation
While IDAM offers many benefits, its implementation can be complex. Challenges include scalability, user resistance, and integration with existing systems.
9. Future Trends in IDAM
As technology continues to evolve, so does IDAM. Future trends include greater use of artificial intelligence for threat detection and a focus on decentralized identity.
10. IDAM in Action: Real-world Examples
Explore how organizations like Amazon and Microsoft have successfully implemented IDAM to protect their data and user accounts.
11. Securing Cloud Environments with IDAM
Cloud computing has transformed the way businesses operate. Learn how IDAM plays a crucial role in securing data in the cloud.
12. IDAM for Small Businesses
IDAM is not just for large enterprises. Discover how small businesses can benefit from implementing IDAM solutions tailored to their needs.
13. IDAM and Compliance
Compliance with data protection regulations is non-negotiable. See how IDAM assists organizations in meeting their compliance obligations.
14. The Human Element: User Training and Awareness
Even the most advanced IDAM system can be compromised through human error. Explore the importance of user training and awareness in maintaining security.
15. Conclusion
In a world where data is a prized asset, Identity Access Management stands as the guardian of our digital borders. By understanding its significance, components, and best practices, organizations can fortify their defenses and embrace a safer digital future.
FAQs
FAQ 1: What are the primary goals of Identity Access Management?
Identity Access Management aims to ensure the right individuals have access to the right resources at the right time, enhancing security and productivity while maintaining compliance.
FAQ 2: Is IDAM only relevant to large organizations?
No, IDAM is relevant to organizations of all sizes. Small businesses can benefit from IDAM solutions tailored to their needs.
FAQ 3: How does IDAM help with compliance?
IDAM helps organizations enforce access policies and audit access, making it easier to demonstrate compliance with data protection regulations.
FAQ 4: What role does user training play in IDAM?
User training is crucial in preventing security breaches caused by human error. It raises awareness and ensures employees use IDAM tools correctly.
FAQ 5: What are some emerging trends in the field of IDAM?
Emerging trends include the use of AI for threat detection, decentralized identity, and increased focus on cloud security.
By embracing Identity Access Management, organizations can fortify their digital defenses and navigate the digital landscape with confidence.
Read another article Facebook Business Suite: Streamlining Your Social Media Management


I believe this is one of the so much important info for me.
And i’m happy studying your article. However want to commentary on few normal things, The
web site style is wonderful, the articles is truly nice :
D. Good process, cheers
I’m curious to find out what blog platform you happen to be working with?
I’m having some small security problems with my latest
blog and I’d like to find something more risk-free.
Do you have any recommendations?
Hello, i think that i saw you visited my blog thus i came to “return the favor”.I’m attempting to find things to enhance my web site!I suppose its ok to use some of your ideas!!
An impressive share! I’ve just forwarded this
onto a co-worker who has been conducting a little homework on this.
And he in fact bought me dinner because I stumbled upon it for him…
lol. So allow me to reword this…. Thank YOU for the meal!!
But yeah, thanks for spending time to talk about this issue here on your site.
I simply could not leave your web site prior to suggesting
that I actually enjoyed the standard info a person provide for your guests?
Is gonna be again regularly to check up on new posts
Simply desire to say your article is as astounding.
The clearness in your post is just spectacular and i could assume you’re an expert on this
subject. Fine with your permission allow me to grab your RSS feed
to keep up to date with forthcoming post. Thanks a million and please keep up
the enjoyable work.
I want to know where exactly to paste the code on my template in my blog so that the ‘Digg It’ Button shows up for each and every post of mine.. . Also If I want to show how many diggs I got on one of my blog post where do I show it? Where exactly do I put the code? And where do I get the code from? Thanks for helping me with this..
Yes! Finally something about vpn coupon code 2024 special coupon code 2024.
An impressive share! I’ve just forwarded this onto a co-worker who has been doing a little homework
on this. And he actually bought me breakfast because I stumbled upon it for him…
lol. So let me reword this…. Thank YOU for the meal!!
But yeah, thanx for spending some time to discuss this subject here on your site.
Also visit my web-site – vpn special
I was suggested this web site by my cousin. I am not sure whether this post is written by
him as nobody else know such detailed about my trouble. You are incredible!
Thanks!
Admiring the hard work you put into your site and detailed information you provide.
It’s awesome to come across a blog every once in a while
that isn’t the same old rehashed information. Great read!
I’ve saved your site and I’m including your RSS feeds to my
Google account.
It’s going to be ending of mine day, but before finish I am reading this fantastic article to increase my knowledge.
Feel free to visit my website :: vpn special code
Awesome post.
Thanks for sharing your thoughts about vpn coupon.
Regards
Thank you, I have recently been looking for info about this subject for a while and yours is the best I’ve found
out till now. However, what in regards to the conclusion? Are you certain concerning the source?
Hello Dear, are you really visiting this website regularly, if so after that you will definitely obtain fastidious know-how.
Thank you a lot for sharing this with all folks you actually realize
what you are talking about! Bookmarked. Please additionally visit my
web site =). We could have a link trade contract among us
Hi mates, its enormous article about educationand completely defined, keep it up all the time.
I got this website from my friend who told me regarding this web site
and now this time I am browsing this website and reading very informative posts at this time.
It’s an awesome post for all the internet viewers;
they will obtain advantage from it I am sure.